Excitement About Risk Management Enterprise
Little Known Facts About Risk Management Enterprise.
Table of ContentsRumored Buzz on Risk Management EnterpriseUnknown Facts About Risk Management EnterpriseRisk Management Enterprise for BeginnersFacts About Risk Management Enterprise RevealedThe smart Trick of Risk Management Enterprise That Nobody is Discussing4 Simple Techniques For Risk Management EnterpriseThe Ultimate Guide To Risk Management Enterprise
Below are a few of its key features that facilities must understand. So, have a look. Real-Time Threat Evaluations and Reduction in this software application permit companies to continuously keep an eye on and evaluate risks as they evolve. This feature leverages real-time data and automated analysis to identify prospective dangers immediately. When dangers are determined, the software application assists in instant mitigation activities.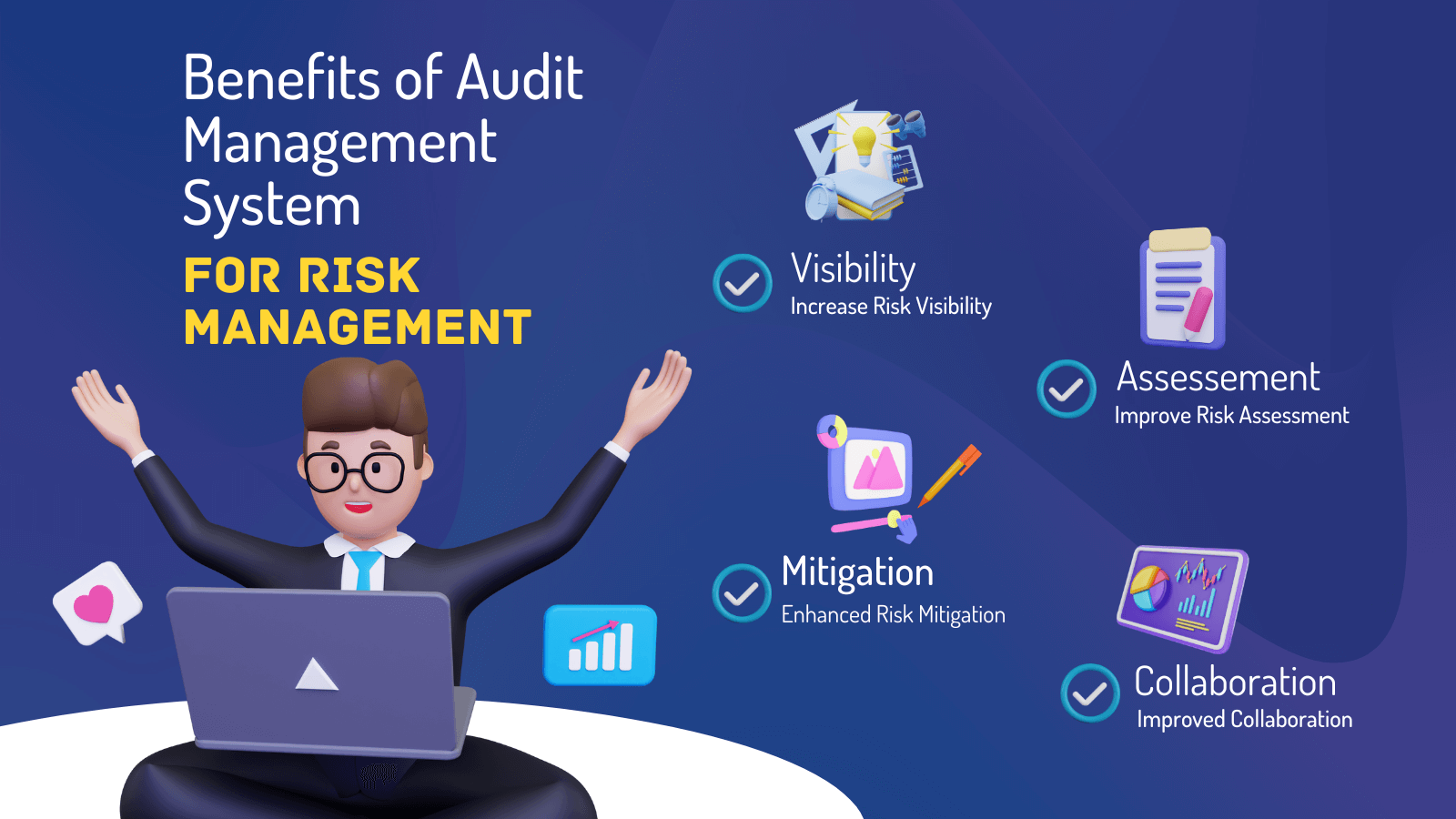
KRIs solve the issue of irregular or uncertain threat assessment. They resolve the obstacle of continuous risk management by offering tools to keep an eye on threats continually. KRIs improve security threat oversight, ensuring that prospective risks are recognized and taken care of efficiently. The job of threat administration must not be an obstacle. Companies have to rely on an excellent and advanced threat monitoring software program.
Top Guidelines Of Risk Management Enterprise
IT take the chance of administration is a part of venture threat management (ERM), designed to bring IT take the chance of in accordance with a company's danger hunger. IT take the chance of monitoring (ITRM) incorporates the policies, treatments and technology needed to lower risks and vulnerabilities, while preserving compliance with appropriate regulative requirements. In addition, ITRM looks for to limit the consequences of devastating occasions, such as safety and security breaches.
While ITRM structures offer valuable guidance, it's simple for IT groups to experience "framework overload." Veronica Rose, ISACA board supervisor and an information systems auditor at Metropol Corp. Ltd., suggests using a mix of structures to accomplish the very best outcomes. For instance, the ISACA Risk IT framework aligns well with the COBIT 2019 structure, Rose claimed.
Business Risk Management Software Development: Perks & Features, Cost. With technological developments, risks are continuously on the surge., companies navigate via a frequently altering sea of risks.
Risk Management Enterprise Fundamentals Explained
In this blog, we will dive right into the globe of ERM software, discovering what it is, its benefits, attributes, and so on to make sure that you can develop one for your organization. Venture Threat Administration (ERM) software is the application program for planning, routing, arranging, and regulating service tasks and streamlining threat management procedures.
With ERM, companies can make informative decisions to improve the overall durability of the business. Dedicated ERM systems are essential for businesses that frequently deal with huge amounts of delicate information and several stakeholders to authorize critical choices.
It can be avoided by making use of the ERM software application system. This system automates law conformity management to keep the organization safe and compliant.
The Facts About Risk Management Enterprise Revealed
You can likewise attach existing software systems to the ERM via APIs or by including data manually. Services can use ERM to evaluate threats based on their potential impact for better threat administration and mitigation.: Including this feature permits individuals to get real-time notifications on their tools regarding any kind of threat that may take place and its influence.
Instead, the software program permits them to set thresholds for various procedures and send press notices in situation of possible threats.: By integrating information visualization and reporting in the custom-made ERM software, companies can obtain clear insights concerning threat trends and performance.: It is mandatory for companies to follow industry compliance and governing standards.
These systems enable firms to implement best-practice threat administration processes that align with market standards, using an effective, technology-driven method to identifying, analyzing, and mitigating risks. This blog site explores the advantages of automatic risk monitoring tools, the areas of risk monitoring they can automate, and the value they bring to an organization.
Some Known Facts About Risk Management Enterprise.
Teams can establish types with the pertinent areas and easily produce different forms for various risk types. These risk assessment types can be flowed for conclusion through automated workflows that send out notifications to the relevant personnel to complete the types online. If types are not completed by the due date, after that chaser emails are immediately sent by the system.
The control monitoring and control testing procedure can likewise be automated. Companies can make use of automatic workflows to send out regular control test notifications and personnel can enter the results using online types. Controls can additionally be monitored by the software application by setting policies to send out signals based on control information held in various other systems and spread sheets that is drawn right into the platform using API assimilations.
Risk monitoring automation software program can additionally sustain with danger coverage for all levels of the venture. Leaders can check out reports on threat exposure and control efficiency with a range of reporting outputs including static reports, Power BI interactive reports, bowtie analysis, and Monte Carlo simulations. The capacity to draw actual time records at the touch of a button removes tough information adjustment tasks leaving danger teams with even more time to examine the data and suggest business on the best strategy.
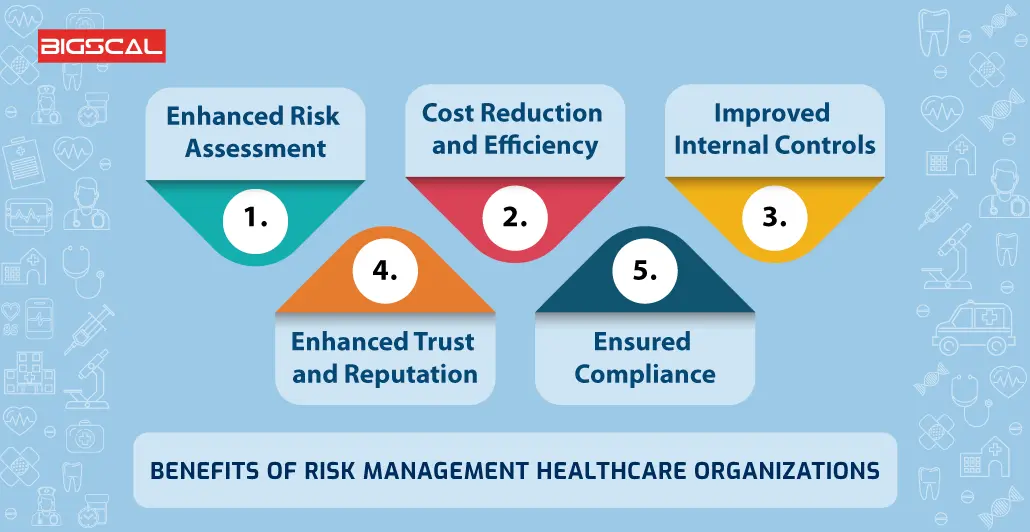
The need for effective has actually never ever been extra important. Risk Management Enterprise. Organizations operating in competitive, fast-changing markets can not pay for delays or inefficiencies in resolving possible threats. Traditional danger administration making use of hand-operated spreadsheet-based procedures, while acquainted, commonly bring about fragmented data, time-consuming coverage, and an enhanced likelihood of human error. Automating the threat management procedure with software addresses these shortcomings.
The Buzz on Risk Management Enterprise
This makes certain danger signs up are constantly current and lined up with business goals. Compliance is an additional critical motorist for automating risk management. Specifications like ISO 31000, CPS 230 and COSO all supply advice around risk monitoring finest practices and control structures, and automated danger administration devices are structured to line up with these needs aiding firms to meet most generally used danger monitoring requirements.
Try to find risk software application systems with a permissions pecking order to easily establish operations for threat rise. This performance enables you to customize the view for every individual, so they only see the data appropriate to them. Make certain the ERM software offers individual monitoring so you can see who entered what data and when.
Seek out devices that offer task threat monitoring capabilities to handle your tasks and profiles and the connected risks. The advantages of adopting threat administration automation software application expand far beyond effectiveness.

Everything about Risk Management Enterprise
While the case for automation is compelling, executing a risk monitoring platform is not without its challenges. For one, information quality is essential. Automated systems rely upon exact, current information to provide purposeful insights. To overcome the challenges of danger management automation, companies should spend in data cleansing and governance to make certain a solid structure for implementing an automated system.
Automation in risk monitoring empowers services to change their method to risk and construct a more powerful structure for the future (Risk Management Enterprise). The question is no more whether to automate threat administration, it's how quickly you can begin. To see the Riskonnect at work,
The solution often exists in exactly how well risks are anticipated and managed. Job administration software application offers as the navigator in the turbulent waters of job implementation, offering tools that determine and evaluate threats and create methods to minimize them check here successfully.